Archive
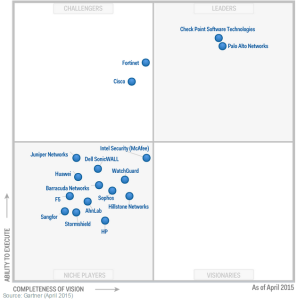
GARTNER Magic Quadrant for Enterprise Network Firewalls 2015
I have just been pleased to find out that I have been working with the right firewall brands over the past 4 years (Palo Alto, Checkpoint and a little bit of Cisco):
Modern firewalls and IPS evasion techniques
I have just had a quick glance on Internet (God bless Google) looking for reviews of evasion techniques to bypass modern firewalls. It’s amazing how vendible all these “independent” security laboratories are! The amount of s$$t some companies manage to pour onto their competitors is beyond any imagination. But as soon as you see some good results you either cannot find exact conditions and configurations used in a test or (surprise!) the winning firewall appears to be manufactured by the same company that created the testing tool and paid for the test 🙂
Though, to be fair, the Evader, being made by Stonesoft (now McAfee), is the most popular tool used to practice IPS evasion techniques.
I found only one resource clearly explaining test conditions and, as a result, the outcome of the test looked fair.
Here is a quick list of popular techniques (details are in the whitepaper referenced above).
- Payload obfuscation and encoding (overcoming simple string matching filters)
- Encryption and tunneling
- Wrapping TCP sequence numbers
- Fragmentation (splitting malicious packets into smaller fragments)
- Protocol violations and decoy trees
So, long story short, if you have an IPS protecting a host you should not assume it’s unbreakable because of this fact and does not require any patching. If you have an unpatched vulnerability exposed to attacks, it’s sudden death is only a matter of time – easy peasy lemon squeezy with most modern IPSes. Here comes a concept of multi-layer protection – use a firewall, IPS, load balancer, web application firewall, patching, secure coding techniques and hardening altogether. Not to mention compulsory professional pen. tests (screw dumb ASV scans! :)) Then you should be good (though it’s all likely to be expensive as you may guess).
Multicast on Checkpoint R76 Gaia + Palo Alto and Cisco
Just finished troubleshooting of multicast issues (no traffic received at all) with a subscriber sitting on a DMZ behind Checkpoint Gaia R76 and source being a couple of hops away behind another firewall – a Palo Alto box. Both firewalls were sitting on top of L2 Cisco kit (Catalysts & Nexuses)
Long story short here are few things to take away from the exercise:
- IPS on that stupid Checkpoint even being globally disabled on the firewall is blocking PIM traffic (hello packets) and thus neighbour relationships do not form on PIM. Solution: enable IPS, find the rule blocking PIM, disable it, disable IPS. LOL!!!
- When you enable IGMP on Gaia boxes which are part of HA group (in this case it was VRRP; ClusterXL might be different) declare your multicast group as local and specify VRRP VIP, not the IP of the box itself;
- Enable PIM not only on the interface facing PIM next hop but also on the interface facing the subscriber (alongside with IGMP) otherwise it looks like Cisco kit is not aware where to send IGMP Joins (which are destined to 224.0.0.22) puts them into a sink hole;
- Pay attention to the IGMP version that you enable on Checkpoint interfaces facing the client. Do a packet capture to double-check. In my case the subscriber was sending v.3 despite the rest of the setup configured for ASM.
As a bonus here is a couple of commands useful on Palo Alto box for some light multicast troubleshooting:
show routing multicast pim neighbour – to see your neighbours
show routing multicast pim statistics – to see your hello packets (both received and sent)
show routing multicast pim state – to see PIM state for your groups
(sorry, omitting Checkpoint stuff as it’s too much writing and I do not really like them – notes above should be sufficient to make it work anyway)