Installing node.js on RHEL 7.1
curl --silent --location https://rpm.nodesource.com/setup_4.x | bash - yum install -y nodejs
(all this fuss is because there is no “native” yum package for Node.js – apparently they do not like Red Hat by a reason! :))
How F5 BigIP may expose your internal IPs
You need to be careful when you configure cookie-based persistence on F5 as by default you advertise this:
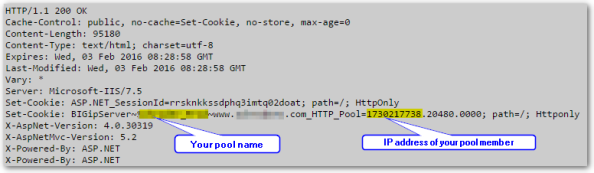 to the whole world. Which is not something you usually want to do 🙂
to the whole world. Which is not something you usually want to do 🙂
Here is how to decode the real IP from the highlighted number:
F5 SOL6917: Overview of BIG-IP persistence cookie encoding
(so the IP on the screenshot seems to be 10.7.33.103 if I did everything correctly)
And this is the fix- F5 SOL14784: Configuring BIG-IP cookie encryption (10.x – 11.x)
F5 BigIP APM (v.12) – SSO using AD & Kerberos – Quick How-To
Here is a quick “how-to” on main principles and practical configuration of Single Sign-On using F5 BigIP. There are quite a few good guides out there on Internet describing how to configure SSO using F5 ADCs in different scenarios. Somehow most of them are focused on the likes of Office 365 and access to public (usually cloud-based) resources from within a company. The cases of hosting of a number of applications with SSO across them are not that well documented by a reason. Relevant configuration guides do exist though. I will try not to repeat them but instead highlight main principles of the approach and also specifics of the version 12 of BigIP firmware.
First of all – the scenario
Assume that we have two web applications exposed to Internet via F5 BigIP appliance. Both applications are hosted on Windows web servers which are members of Active Directory domain (they could well be running a Linux configured to authenticate in Windows via RADIUS, for instance – does not really matter). I used Windows Server 2012 but earlier versions 2008 and 2003 should work equally well. Read more…
Deploying F5 BigIP in Microsoft Azure
This is a real pain the @r$e. Forget all your habits acquired in the happy world of VMWare or on physical BigIP boxes. Azure is nothing like this. It’s all about limitations.
In fact all of them stem from the fact that you can have only one interface on your F5 VE box in Azure. One for everything – management, SNAT and all of your VSs. Yes, you have heard me correctly – all these pieces have to survive on the single interface and single IP address. Arrghhh!… Read more…
VMware released a free web client for ESXi
Very nice!
http://www.vladan.fr/esxi-free-web-client-interface/
Though I wonder why? Are they going from ESXi back to ESX roots? :)))
CIS RHEL hardening script – fixing non-working Sed expressions (unknown option to `s’)
I do not know what they were thinking about (and testing!) but the sed regular expressions below did not work on neither of my instances of RHEL (CIS remediation script version 1.4.0):
# Set nodev option for /tmp Partition
echo
echo \*\*\*\* Set\ nodev\ option\ for\ /tmp\ Partition
egrep -q “^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$” /etc/fstab && sed -ri “s/^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$/\1/tmp\2nodev\3\4/” /etc/fstab# Set nosuid option for /tmp Partition
echo
echo \*\*\*\* Set\ nosuid\ option\ for\ /tmp\ Partition
egrep -q “^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$” /etc/fstab && sed -ri “s/^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$/\1/tmp\2nosuid\3\4/” /etc/fstab# Set noexec option for /tmp Partition
echo
echo \*\*\*\* Set\ noexec\ option\ for\ /tmp\ Partition
egrep -q “^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$” /etc/fstab && sed -ri “s/^(\s*\S+\s+)/tmp(\s+\S+\s+\S+)(\s+\S+\s+\S+)(\s*#.*)?\s*$/\1/tmp\2noexec\3\4/” /etc/fstab
All of them were throwing a very annoying:
sed: -e expression #1, char 61: unknown option to `s'
Fixing Armitage in Kali Linux 2.0
Sadly Armitage is failing in the fresh install of Kali 2.0 but fortunately there are always good guys who fix all troubles.
Here is the one for this particular issue:
https://github.com/ompster/kali2_fixer (the link opens in the new window)
or, to save you a few minutes, here is what you need to do:
git clone https://github.com/ompster/kali2_fixer.git cd kali2_fixer/ python kali2_fix.py
The script will offer you a number of options with Armitage fix amongst them. In essence it just pulls an up to date version of Armitage where all dependencies are fixed.
PAM module for GeoIP login restrictions
Found a very nice PAM module (can be used with SSH etc) that can provide login restrictions based on user geo-location as per official internet registrars’ stats files. It’s probably not as good as its commercial rivals but does the job if you’re not too picky! It can also block logins in a LAN based on source MAC or IP addresses.
https://github.com/ColumPaget/pam_ihosts (the link opens in new browser window)
Red Hat Enterprise Linux 7.1 in VirtualBox – quick setup for a PoC
Obviously it’s not a tutorial – neither for VirtualBox nor for Linux – just a quick note on essentials when you need to provision a RHEL instance in VirtualBox without active Red Hat subscription.
I assume you have installed a basic server with GUI. Then it’s really important and convenient to have Guest Additions installed (this is basically an analogue of VMWare Tools allowing for better integration between VM and the host OS). Read more…
Legal aspects of non-repudiation in digital world
Just read an interesting research paper on various aspects of non-repudiation in the context of digital environments .
Authors discuss legal aspects in different legal systems and come to a conclusion that:
… deployment of a trusted computing system for digital signatures is the only secure option, resulting in a legal position where the onus of proof for the electronic environment is equivalent to the paper-based environment. If a trusted computing system is used to affect a digital signature, then and only then can the onus of proof lie with the recipient in the same manner that exits in the paper-based world. Without a trusted computing system, neither party – the signer or the recipient – is in a position to produce the necessary evidence to prove their respective case.
MCCULLAGH, Adrian; CAELLI, William. Non-repudiation in the digital environment. First Monday, [S.l.], aug. 2000. ISSN 13960466. Available at: <http://www.firstmonday.org/ojs/index.php/fm/article/view/778/687>.
p.s. Not that I really enjoy reading this sort of essays but this one came really useful while I was working on a RFP response…